Residential Network Installation
Residential Network Installation Services: Connecting Your Home with Seamless Technology
In today’s fast-paced, digital world, a reliable and efficient home network is more important than ever. From streaming movies and playing video games to working from home and managing smart devices, our homes are increasingly dependent on the internet. That’s where professional residential network installation services come in. Whether you’re setting up a new network or upgrading an existing one, a skilled technician from Microlenk Technologies can ensure you have a fast, secure, and dependable connection.
Commercial Network Installation
Commercial Network Installation Services: Ensuring Reliable and Scalable Connectivity for Your Business
In today’s fast-paced business environment, a reliable and secure network infrastructure is the backbone of every modern enterprise. Whether you're running a small office or a large corporate campus, having a robust network installation is critical for supporting daily operations, improving collaboration, and driving productivity. Professional commercial network installation services provide businesses with the expertise to create a high-performing network that meets both current and future needs.
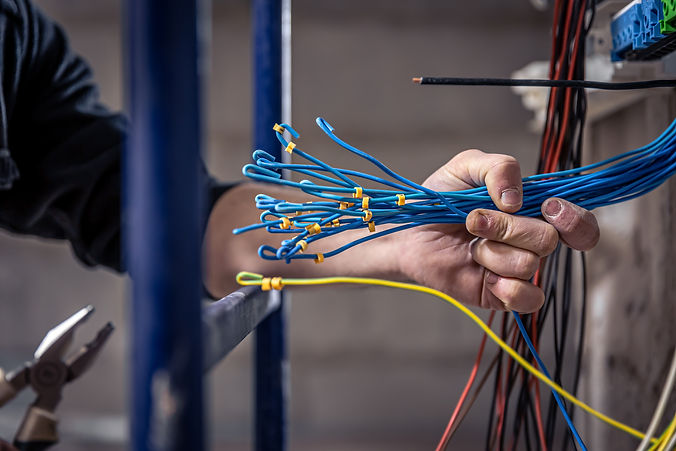
Network Cable Installation Services
Looking for professional network cable installation services? Our expert team specializes in providing high-quality, reliable, and efficient network cabling solutions for homes and businesses. Whether you need new network installations, upgrades, or repairs, we ensure fast and secure connections with minimal disruption to your daily operations. We offer a range of services including structured cabling, fiber optic installation, data cabling, and more, all tailored to meet your specific requirements. Trust our experienced technicians to deliver top-notch service, ensuring your network is set up for optimal performance and future scalability. Contact us today for a free consultation and expert advice on your network cable installation needs!

Brainerd Lakes Area Telecommunications Service Provider
Microlenk Technologies is a leading telecommunications service provider in Brainerd, MN, offering reliable, high-speed connectivity solutions to businesses and residents in the area. With a commitment to delivering cutting-edge technology and exceptional customer service, Microlenk ensures that clients experience seamless communication, fast internet speeds, and dependable support. Whether you're a small business seeking a secure network infrastructure or a homeowner in need of fast internet, Microlenk Technologies has the expertise and resources to meet your needs. We offer a range of tailored solutions, from fiber-optic broadband to managed services, ensuring Brainerd stays connected in today’s digital world.

Is your Network Secured and Protected
Microlenk Technologies provides professional Network Security Solutions while utilizing industry standard Network Equipment from manufactures such as SonicWall and UniFi. In today’s digital landscape, businesses rely heavily on networks to ensure efficient operations, seamless communication, and collaboration. However, as businesses grow and integrate new technologies, network security becomes a critical concern. Securing business networks is not just about protecting sensitive data but ensuring business continuity, protecting against cyber threats, and maintaining trust with clients and partners.

Protecting Your Network and Information
In today’s digital age, securing your network and private data has become more crucial than ever. With increasing threats from cybercriminals, hackers, and data breaches, safeguarding your personal and business information is essential to maintaining privacy and security. Whether you're using the internet for work, entertainment, or communication, knowing how to protect your network and data is key to reducing vulnerabilities and preventing attacks.
Your SonicWall Installation Experts
Join the thousands of companies who depend SonicWall for there Network Security needs. SonicWall is a leader in the Network Security industry, and Microlenk Technologies is proud to support and install SonicWall products.
We Proudly Service and Install SonicWall and UniFi
SonicWall Networks
SonicWall is a recognized leader in network security, providing comprehensive firewall protection and other cybersecurity solutions to businesses of all sizes. For over three decades, SonicWall has been dedicated to offering innovative security technologies to combat emerging cyber threats, ensuring the safety of corporate networks, applications, and data.
UniFi Networks
UniFi Networks, developed by Ubiquiti Networks, focuses on providing high-performance, scalable, and easy-to-manage networking solutions. UniFi products are known for their affordability, reliability, and ease of use, making them popular with businesses, educational institutions, and even home users who need high-quality networking infrastructure.
UNDERSTANDNG NETWORK TYPES
A business network refers to the infrastructure that enables communication, data sharing, and collaboration within an organization and with external entities such as customers, suppliers, and partners. It consists of various components, including:
-
Local Area Networks (LANs): These are private networks used within a business to connect employees, workstations, servers, and other devices within a specific geographic area, such as an office building or campus.
-
Wide Area Networks (WANs): These networks connect multiple LANs across various locations, enabling communication between offices, remote workers, and clients worldwide.
-
Cloud Networks: With the rise of cloud computing, businesses are increasingly adopting cloud-based systems, which enable data storage, applications, and collaboration tools to be accessed from anywhere.
-
Virtual Private Networks (VPNs): VPNs provide secure remote access to a company’s network, especially for employees working from home or traveling.
-
Wireless Networks (Wi-Fi): These networks allow devices to connect wirelessly to a business’s internal network or the internet, providing flexibility and mobility to employees.
The efficiency, functionality, and scalability of these networks play a vital role in the success of a business, allowing for data exchange, communication, and access to critical resources.
UNDERSTANDNG NETWORK TYPES
A business network refers to the infrastructure that enables communication, data sharing, and collaboration within an organization and with external entities such as customers, suppliers, and partners. It consists of various components, including:
-
Local Area Networks (LANs): These are private networks used within a business to connect employees, workstations, servers, and other devices within a specific geographic area, such as an office building or campus.
-
Wide Area Networks (WANs): These networks connect multiple LANs across various locations, enabling communication between offices, remote workers, and clients worldwide.
-
Cloud Networks: With the rise of cloud computing, businesses are increasingly adopting cloud-based systems, which enable data storage, applications, and collaboration tools to be accessed from anywhere.
-
Virtual Private Networks (VPNs): VPNs provide secure remote access to a company’s network, especially for employees working from home or traveling.
-
Wireless Networks (Wi-Fi): These networks allow devices to connect wirelessly to a business’s internal network or the internet, providing flexibility and mobility to employees.
The efficiency, functionality, and scalability of these networks play a vital role in the success of a business, allowing for data exchange, communication, and access to critical resources.
NETWORK BEST PRACTICES
To protect business networks, it’s essential to adopt a comprehensive network security strategy that combines technology, policies, and employee awareness. Some best practices include:
-
Implement a Layered Security Approach: Relying on a single security tool or solution is not enough. A layered approach combines firewalls, encryption, antivirus software, intrusion detection, and access controls to provide multiple lines of defense.
-
Employee Training: Employees should be educated about the latest cyber threats and how to recognize phishing attempts, social engineering, and suspicious activity. Human error remains one of the most common causes of data breaches.
-
Regular Audits and Assessments: Regular network security audits help identify vulnerabilities and weaknesses in the network infrastructure. Penetration testing, vulnerability scanning, and risk assessments are key components of a robust security strategy.
-
Data Backup and Disaster Recovery Plans: Regularly backing up data and having a disaster recovery plan in place ensures that businesses can recover quickly in the event of a cyberattack, such as a ransomware attack or hardware failure.
-
Compliance with Regulations: Many industries are subject to regulatory standards, such as GDPR, HIPAA, and PCI-DSS, that mandate specific network security practices. Ensuring compliance with these standards not only helps safeguard data but also protects the business from legal repercussions.
-
Zero Trust Architecture: The zero-trust model assumes that every user or device, whether inside or outside the organization’s network, could be a potential threat. This approach requires continuous verification of all users and devices attempting to access the network.
THE GROWING NETWORK THREAT LANDSCAPE
The landscape of cyber threats has evolved, becoming more sophisticated and persistent. Businesses of all sizes are vulnerable to attacks such as:
-
Phishing Attacks: Cybercriminals use fake emails, websites, or other communication methods to trick users into providing sensitive information such as login credentials, financial details, or personal data.
-
Ransomware: This malicious software locks or encrypts a victim’s data and demands payment for its release. Ransomware attacks have been on the rise, affecting organizations in all sectors.
-
Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks: These attacks overwhelm a network with traffic, causing it to crash and disrupting business operations.
-
Man-in-the-Middle (MITM) Attacks: In these attacks, a cybercriminal intercepts communications between two parties, often with the goal of stealing sensitive data or injecting malicious content.
-
Insider Threats: These threats come from employees or contractors who intentionally or unintentionally compromise network security, either through negligence or malicious actions.
As businesses increasingly depend on technology, the potential impact of these threats on a network grows exponentially. A breach could lead to data theft, financial loss, service disruptions, or damage to an organization’s reputation.